Next-Generation Antivirus takes advanced level of endpoint security protection.
It goes beyond known file-based malware signatures and heuristics because it’s a
system-centric, cloud-based approach.


What is End Point Protection
Endpoint security is the practice of securing endpoints or entry points of end-user devices such as desktops, laptops, and mobile devices from being exploited by malicious actors and campaigns. Generally, an endpoint security software operates using an agent-server communication model. The agent application is installed on all the endpoints and it regularly collects and updates data, such as, unpatched vulnerabilities, missing patches, etc.
Why we need End Point Protection for our organization?
Endpoint security is one of the most efficient ways to prevent these weak spots from becoming an actual security threat. Insider threats can also be completely unintentional. Someone can unknowingly cause a breach in security and may not ever know that they’ve compromised the entire system.
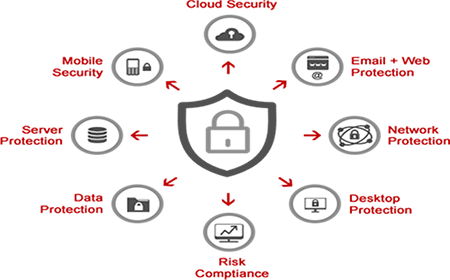
Features of End Point Protection